Directory Services User Management
Directory Services User Management
From myObjectiveOLAP Server 3.0.1 third party Directory Services authentication is supported as a means of authenticating client connections and allowing for myObjectiveOLAP access to be managed by your existing support teams.
Heterogeneous installations using Directory Services and Native User Store are also supported. Native User management is still supported and will continue to be so.
Overview of Directory Services Implementation
The following diagram details the implementation of the Directory Services myObjectiveOLAP Server implementation.
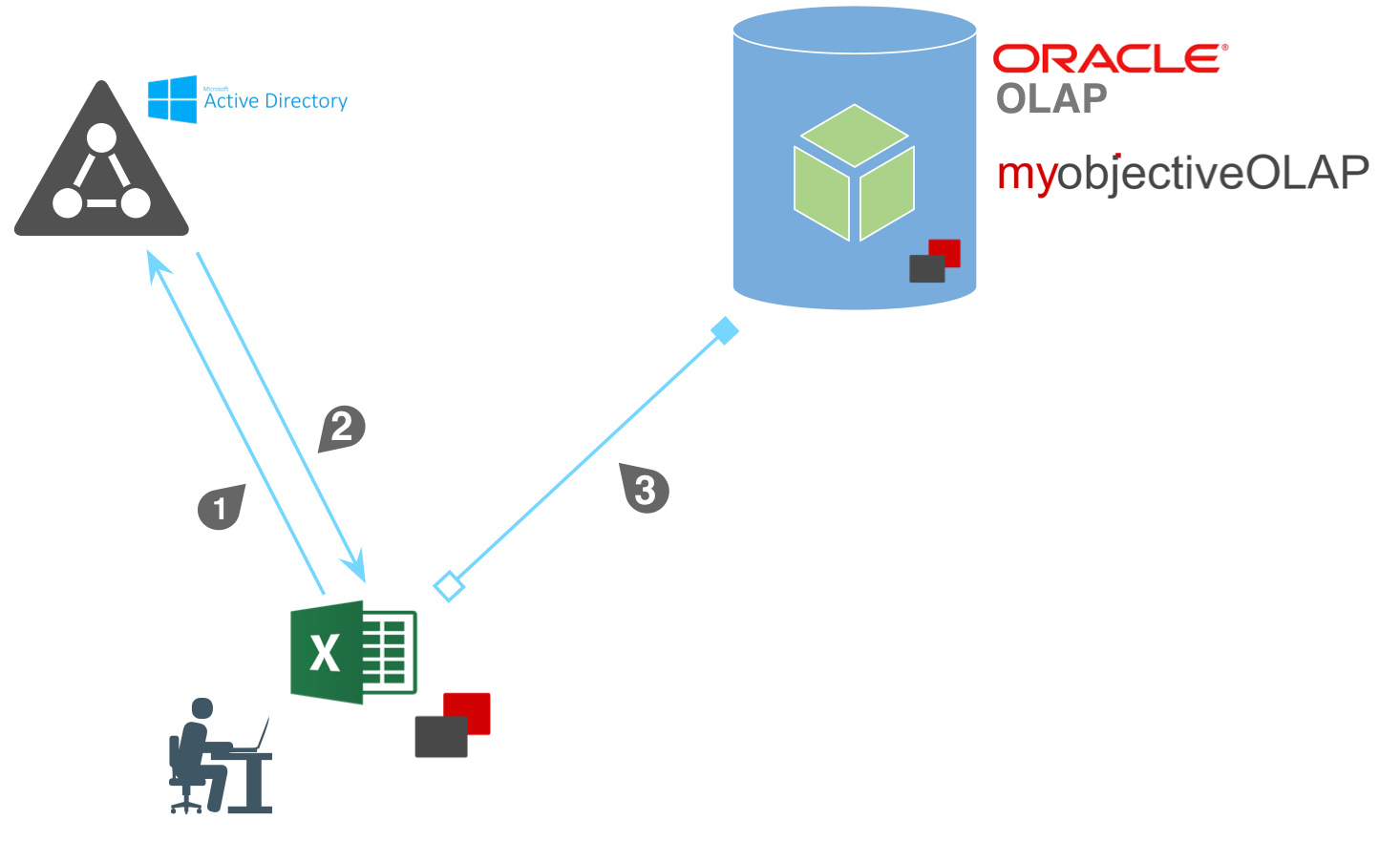
Step |
Description |
1 |
End user starts the logon process to myObjectiveOLAP. The myObjectiveOLAP client contacts the domain and validates the users username & password. |
2 |
Group membership information is passed to the myObjectiveOLAP client application. User details are also retrieved e.g. Site, Description, Telephone Number, Email, First Name, Surname |
3 |
[Providing Username and Password correct in Step 1] myObjectiveOLAP initiates a connection with the myObjectiveOLAP Server and passes the information to the myObjectiveOLAP native user store and configures user profile based on group membership details. |
Configuring myObjectiveOLAP for Directory Services Authentication
To configure myObjectiveOLAP for Directory Services Authentication you will need to update your mooApplicationSettings.xml file adding two new keys:
Authentication Keys
ACTIVED_AUTHENTICATION
Key Values Boolean [TRUE/FALSE] Determines whether Directory Services Authentication should be used. DEFAULT: Disabled, Native User Management in Effect
ACTIVED_AUTHENTICATION_DOMAIN
Key Value String. Name of your Domain. DEFAULT: Disabled, Native User Management in Effect
You can copy and paste the following into your application settings file, adding your domain name details.
<Settings>
<Key>ACTIVED_AUTHENTICATION</Key>
<Value>TRUE</Value>
</Settings>
<Settings>
<Key>ACTIVED_AUTHENTICATION_DOMAIN</Key>
<Value>YOUR_DOMAIN_NAME</Value>
</Settings>
Our example settings file is shown below:
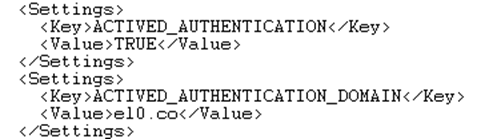
Your mooApplicationSettings.xml file is only read on start-up of the client application (Excel). If you have already started the Excel session you wish to connect from you should restart Excel.
Creating Standard Groups
A minimum of two groups are required for Directory Services authentication.
Group |
Description |
myObjectiveOLAP |
End user group, user does not have access to any administration functions |
myObjectiveOLAPAdmin |
Admin group, user can access all functionality, including process, workflow, and session management. |
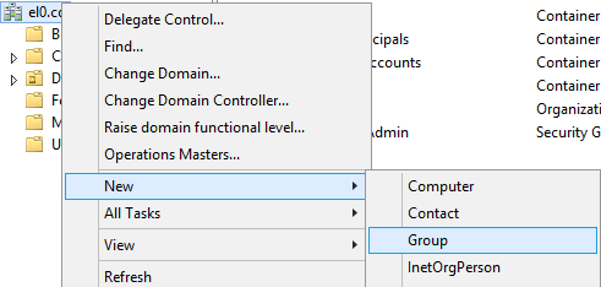
These should be created as follows (example shows creating users and groups through the Windows Server 2012 Active Directory Users and Computers control):
1) Create a new Group:
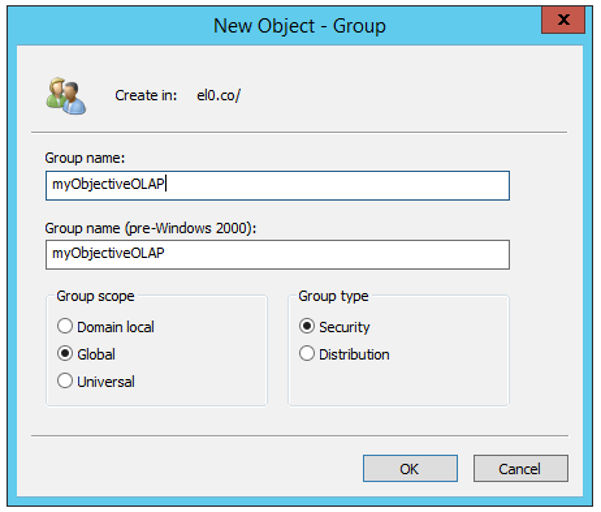
2) Call the new group "myObjectiveOLAP"
3) Repeat Step 1 & 2, but create this group as "myObjectiveOLAPAdmin"

Creating a User and Assigning to the myObjectiveOLAP Groups
In this example we will go through the steps of creating a brand new user and provisioning them for myObjectiveOLAP access
1) Create a new user
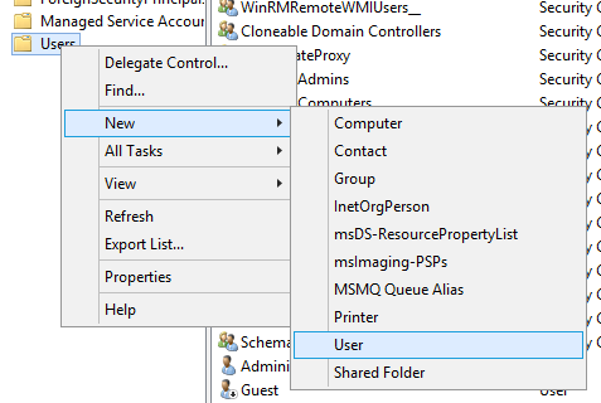
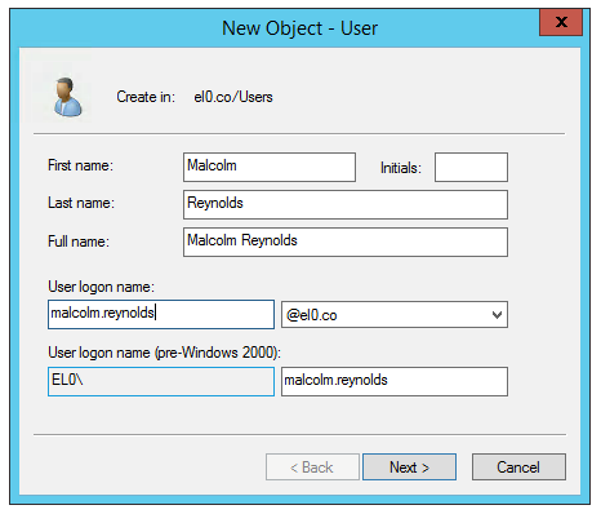
2) Complete basic information about our new user
3) Set an initial password.
IMPORTANT: In a real world scenario you will probably select "User must change password at next logon". If you are testing and not planning to logon to a computer to change the password before attempting to access myObjectiveOLAP you should un-check this box as Active Directory will not authenticate any third party authentication until the password has been changed.

4) Finish

5) Edit our users properties
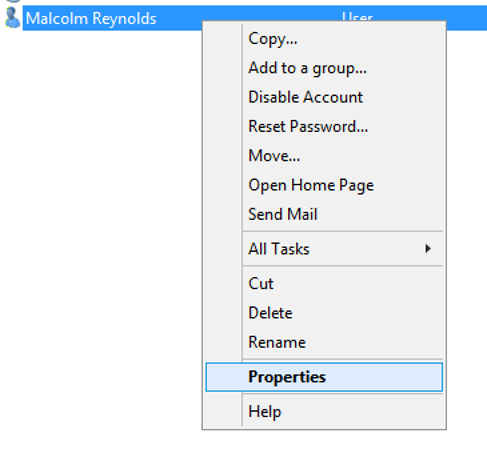
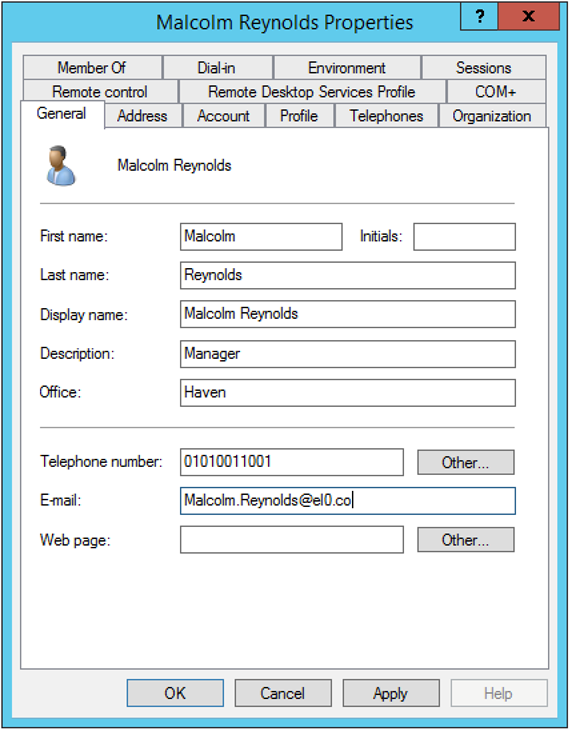
6) Complete more detailed information about our test user in General
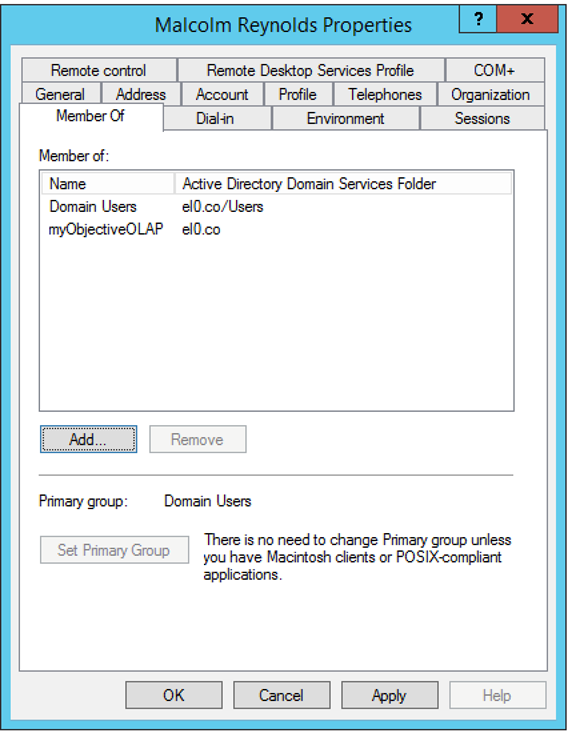
7) Assign our myObjectiveOLAP groups to our user in the Member Of pane.

Click Add

Type "myObject" and choose Check Names:
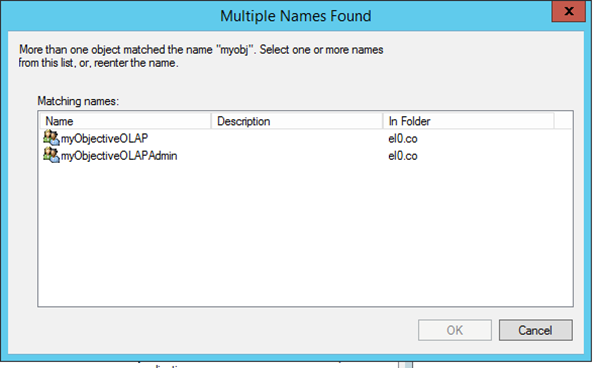
Select the end-user myObjectiveOLAP group and press OK
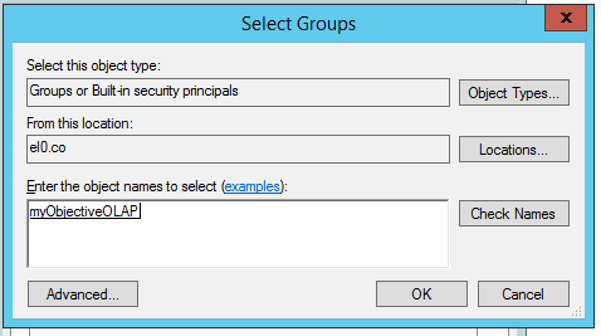
and OK.
Now press Apply:
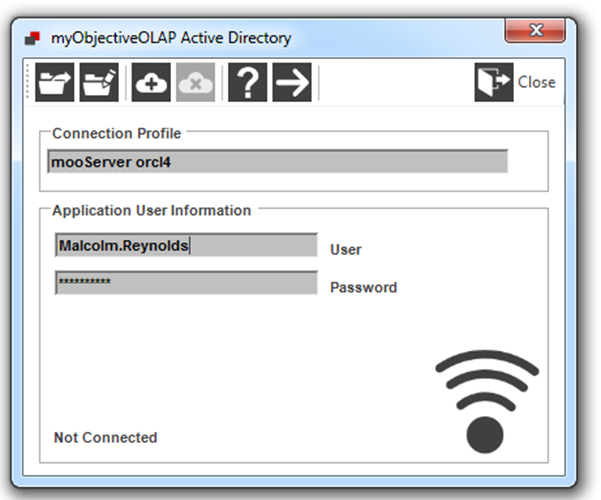
Now open the myObjectiveOLAP logon screen and enter your Active Directory username and password as you have configured:
If we now look at the Native Store manager:
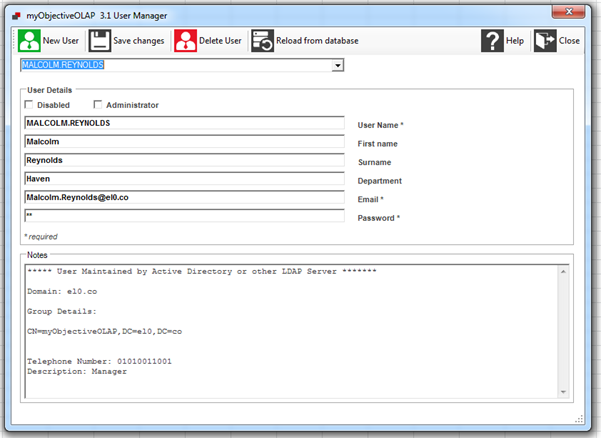
All of the data has been synced with the Directory Services record, and the user is flagged as being managed by Active Directory.